Accessing AWS EC2 Files With SMB Over SSH
The problem
Recently I had to spin up a couple of Ubuntu EC2 instances for development work. However, I didn’t want to give up the comfort of my familiar graphical editor on the laptop, nor install additional software on my local system.
The solution
 Setup EC2 instance
Setup EC2 instance
Enable ssh port forwarding
Add the following lines to /etc/ssh/sshd_config
Restart sshd
Enable Samba
Make a backup of the Samba config file
Create a Samba share
Add the following lines to /etc/samba/smb.conf
Restart smb and test the config file
Setup local system
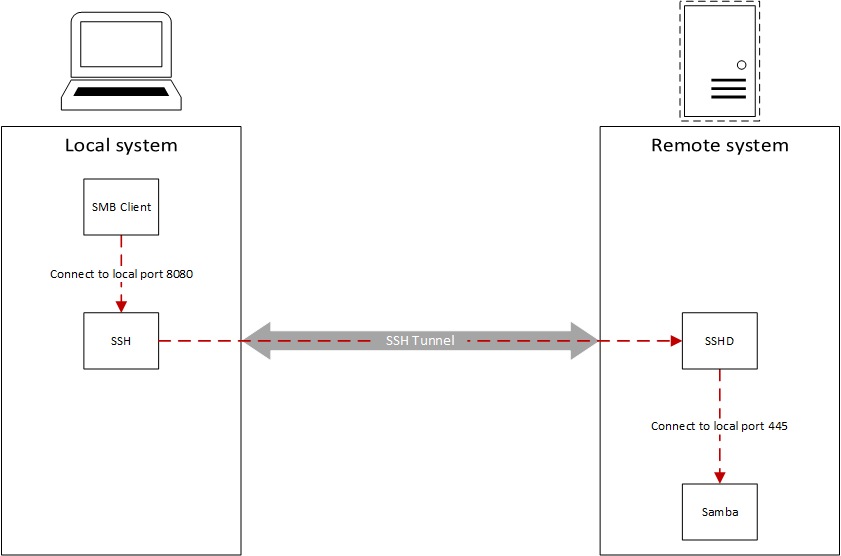
Start ssh port forwarding
We can now connect to EC2’s SMB share using
Notes
Recently I had to spin up a couple of Ubuntu EC2 instances for development work. However, I didn’t want to give up the comfort of my familiar graphical editor on the laptop, nor install additional software on my local system.
The solution
 Setup EC2 instance
Setup EC2 instanceEnable ssh port forwarding
Add the following lines to /etc/ssh/sshd_config
# Port forwarding
AllowTcpForwarding yes
AllowTcpForwarding yes
Restart sshd
sudo /etc/init.d/ssh restart
Enable Samba
sudo apt-get install samba
sudo smbpasswd -a <user name>
sudo smbpasswd -e <user name>
sudo smbpasswd -a <user name>
sudo smbpasswd -e <user name>
Make a backup of the Samba config file
sudo cp /etc/samba/smb.conf /etc/samba/smb.conf.bk
Create a Samba share
Add the following lines to /etc/samba/smb.conf
[share]
path = <path to share directory>
valid users = <user name>
read only = no
path = <path to share directory>
valid users = <user name>
read only = no
Restart smb and test the config file
sudo service smbd restart
testparm
testparm
Setup local system
Start ssh port forwarding
sudo ssh -L 8080:localhost:445 -i ~/.ssh/id_rsa <username>@<EC2 instance IP>
We can now connect to EC2’s SMB share using
smb://127.0.0.1:8080 (MacOS) or \\127.0.0.1:8000 (Windows)
Notes
- Instead of tunneling SMB over SSH, we could have installed sshfs (requires FUSE)
- I blame Cornell CS for my unhealthy addiction to Visual Studio but that’s another story for another time…